exactly the same security stack operates where ever deployed for an unprecedented amount of regularity when applying security procedures.
the first administrator can make numerous administrative-user IDs, granting Each individual ID the best to deal with only precise domains. You may as well configure the appliances to perform automated updates to BIND and the Linux OS, even further decreasing the executive workload.
A device that may still use Electricity in the shape of lights or other shows exhibiting the device is off
it is possible to Choose between various firewall appliances, according to your requirements. inside of a multi-billion dollar network security firewall current market scheduled to reach $10.5Opens a different window
location your ceiling enthusiast effectively will make a large change With regards to cooling, but there's a more standard way to reduce electricity use all yr-round -- unplugging appliances like your Television, Computer system, printer, espresso maker as well as your electric powered toothbrush.
according to the device, you can defend any networked system from enterprise servers to household IoT devices.
There's two forms of firewalls – stateless and stateful – where by the latter is more open to customization and complexity.
Adonis's security options consist of help for BIND 9 encrypted zone transfers and TSIGs to authenticate zone transfers as well as other DNS updates. Data-validation equipment look more info for reasonable errors in DNS configurations and guarantee entire and accurate synchronization and replication with slave servers.
purchasing a clever plug will help you preserve Vitality by managing the ability on nearly any device you plug in. This plug from Leviton is CNET's leading decide on.
a powershell brand close to the text powershell tips and tricks midyear roundup on a tech themed history
Businesses of all dimensions As well as in each individual vertical use pfSense additionally - Primarily individuals who expect options present in enterprise-class solutions, at finances-friendly purchaser / SMB stage cost factors.
If you're thinking that you are scammed, the primary port of get in touch with when possessing an issue is to easily request a refund. Here is the to start with and least complicated phase to find out regardless if you are dealing with a real corporation or scammers.
just about every network is actually a snowflake. No two are alike. Sooner or later on you'll need help. we've been in this article. assist subscriptions for small business assurance and relief. Deep documentation of each nook and cranny. Professional solutions and teaching from anyone who has worn your sneakers.
In this list of top 10 firewall hardware devices, We now have protected the ideal solutions for the most common use cases (organized in alphabetical order).
 Alana "Honey Boo Boo" Thompson Then & Now!
Alana "Honey Boo Boo" Thompson Then & Now! Judd Nelson Then & Now!
Judd Nelson Then & Now! Seth Green Then & Now!
Seth Green Then & Now! Macaulay Culkin Then & Now!
Macaulay Culkin Then & Now!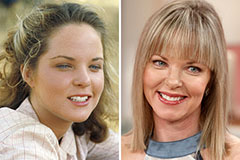 Melissa Sue Anderson Then & Now!
Melissa Sue Anderson Then & Now!